In this new tutorial dedicated to IIS ARR, I will explain how to configure ARR in order to be able to use a self-signed certificate on the target server.
In the previous tutorial, I explained how to do an SSL dump, in this configuration the target server is in HTTP, which means that the request between ARR and the target server is unencrypted.
Today more and more applications default to HTTPS (SSL) like Exchange.
Here the idea is to leave the self-signed certificate on the target server and put a valid certificate on ARR so that the traffic is re-encrypted.
With an unknown certificate from the ARR server, you will have a 502 error page like below from an Internet browser:
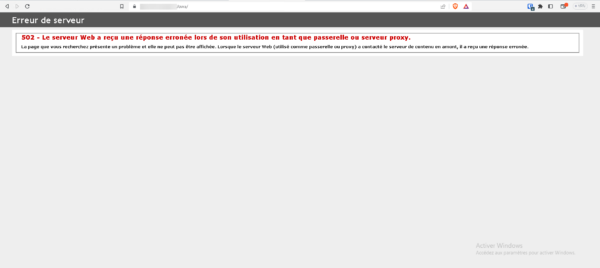
At first glance, the 502 error may suggest that the destination server is not available.
As a security measure, the error pages sent by IIS only return a standard error code. To have more information on the 502 error, you must go through a browser on the ARR server itself to have all information.
Here is the same query page with the same error on the ARR server:
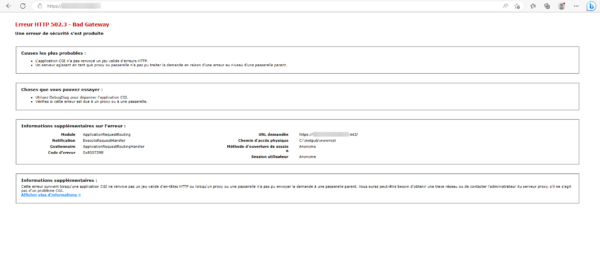
This time we have a little more information about the error, the full error code is 502.3 – A security error has occurred. This error is due to the fact that the target server certificate is not valid.
From there, there are several solutions:
- Install the certificate(s) of the target servers in the IIS server store
- Install valid and recognized certificates
- Tell IIS ARR to ignore this error
In this tutorial, we will see the third option, for this we must add a registry key to the server: SecureConnectionIgnoreFlags.
By default the registry key does not exist, it must be created in the following location:
HKEY_LOCAL_MACHINE\ SOFTWARE\Microsoft\IIS Extensions\Application Request Routing\ParametersIt may also be necessary to create the Parameters key
Then create a 32-bit DWORD Value key named SecureConnectionIgnoreFlags.
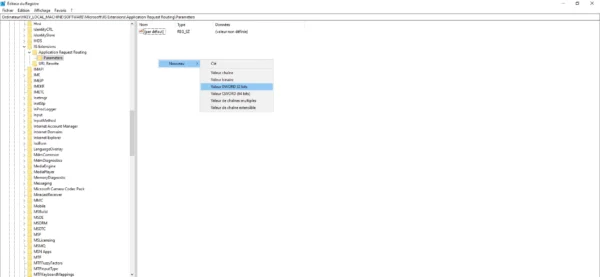

You can also use this command line to create the key:
reg.exe add "HKLM\SOFTWARE\Microsoft\IIS Extensions\Application Request Routing\Parameters" /v SecureConnectionIgnoreFlags /t REG_DWORD /d 0Now, we will modify the value of the key to 300:


The value 300 tells ARR to ignore the unknown certificate error and certificate misuse.
Here is the list of possible values:
| Valeur | Description |
|---|---|
| 0x00001000 | SECURITY_FLAG_IGNORE_CERT_CN_INVALID (DEFAULT) |
| 0x00002000 | SECURITY_FLAG_IGNORE_CERT_DATE_INVALID |
| 0x00000100 | SECURITY_FLAG_IGNORE_UNKNOWN_CA |
| 0x00000200 | SECURITY_FLAG_IGNORE_CERT_WRONG_USAGE |
The values can be added to ignore several errors, if you want to ignore all errors, you can use the value 3300 for example.
Once the registry key is configured, restart IIS using the iisreset command.
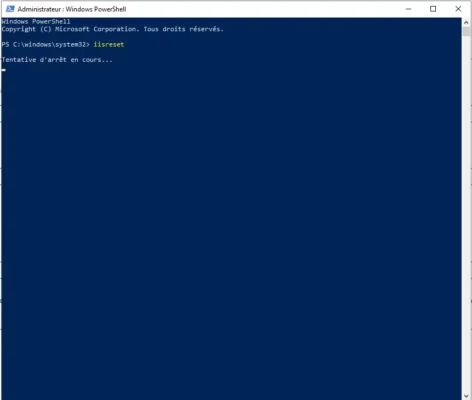
You should no longer get a 502 error from the browser.