In this tutorial, I will explain to you how to activate extended protection (Exchange Extended Protection) on Exchange 2016 (and 2019 if you do not have CU14 which automatically activates it) which will allow you to protect yourself from CVE-2024 -21410.
Exchange Extended Protection is in fact an enhanced security configuration for Exchange 2016 / 2019. This configuration is applied using a PowerShell script.
Before explaining how to apply this extended protection, there is a particularly important point of attention which is how you publish your Exchange servers.
If you use an IIS ARR / Kemp / F5 type reverse proxy solution… there must be no SSL offload between the reverse proxy and the Exchange servers, the communication must be in HTTPS from the client to the Exchange server . Second element to take into account, the SSL certificate must be the same on the Reverse proxy and the Exchange server(s).
Before starting the extended protection configuration for Exchange, the SERVER\RPC site (Default Web Site) must be configured without SSL Offloading.
To do this, enter the following EMS command:
Set-OutlookAnywhere 'EXCHANGE-SERVER-X\RPC (Default Web Site)' -SSLOffloading $false -InternalClientsRequireSsl $true -ExternalClientsRequireSsl $trueAdapt the command by modifying EXCHANGE-SERVER-X to make it fit your environment; this command must be placed for each Exchange server.
To see the result of Exchange Extended Protection we will first use the script HealthChecker.ps1 which will allow us to check the health of the Exchange environment.
Upload the script to an Exchange server and run in EMS .\HealthChecker.ps1.
The result of the Security Vulnerability part:
Security Vulnerability
----------------------
IIS module anomalies detected: False
Security Vulnerability: Download Domains are not configured. You should configure them to be protected against CVE-2021-1730.
Configuration instructions: https://aka.ms/HC-DownloadDomains
Security Vulnerability: CVE-2022-24516, CVE-2022-21979, CVE-2022-21980, CVE-2022-24477, CVE-2022-30134, CVE-2024-21410
Extended Protection is not configuredIn the logs, we can see that Extended Protection is not activated and that the server is vulnerable to several CVEs including the CVE-2024-21410.
We will now apply Extended Protection to protect against the various CVEs of Exchange servers.
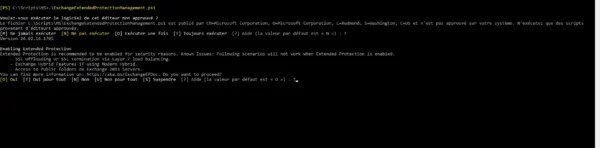
Download the script ExchangeExtendedProtectionManagement on an Exchange server.
Extended Protection will be applied to all Exchange servers.
From the EMS console, run the script as administrator.
.\ExchangeExtendedProtectionManagement.ps1When launching the script, you must confirm execution twice:
- The first to validate the editor who signed the script
- The second to confirm the warning message about known issues.
Wait while the script executes…

You have enabled Exchange Extended Protection.
To see the result, restart the script .\HealthChecker.ps1
If we look in the Security Vulnerability section, the vulnerabilities covered by Exchange Extended Protection are no longer listed, notably CVE-2024-21410.

Now test the different OWA and Outlook client access to make sure everything is working correctly.
In the event of a complete blockage, it is possible to deactivate extended protection:
.\ExchangeExtendedProtectionManagement.ps1 -DisableExtendedProtectionTo go back (Rollback):
.\ExchangeExtendedProtectionManagement.ps1 -RollbackType "RestoreConfiguration"