In this tutorial, I will show you how to block PowerShell remote access to Exchange with ARR.
As a security measure, if you use IIS ARR to publish Exchange servers to the Internet, you must block PowerShell remote access.
By default, it is possible to remotely administer an Exchange server with PowerShell, we find all the Cmdlets available in EMS (Exchange Management Shell).
On the ARR server, launch the IIS console and go to the list of rewrite rules. You should have something, like the screenshot above:

We will now create a rule that will block access to the URL containing powershell.
In the action area, click on Add rules 1.

The rule will manage incoming traffic, click on Empty rule 1 then on the OK button 2.

Name the rule 1, select Matches pattern 2 then choose Regular expressions 3. In the Model field enter ^powershell.* 4..

We will now define the conditions for applying the rule, expand the Conditions 1 area and click on the Add 2 button.

Here we will define the URL(s) which are used to publish the Exchange servers. In the Condition Entry field, put {HTTP_HOST} 1 and in the model field indicate the URLs 2 then click on OK 3 to create the condition.
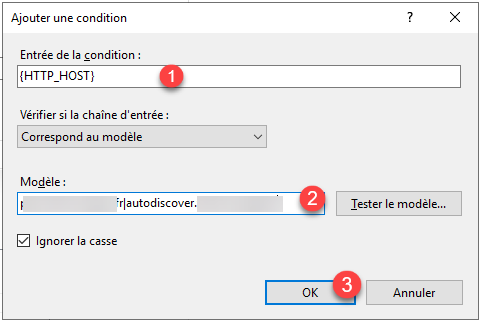
If you have several URLs to put, they must be separated by pipe |.
The condition is added 1, this is the only condition that we will apply.

We still have the action to define to block requests, expand the Action 1 box, action type: select Custom response 2, then indicate the status code 503 3 and in the Reason and description of the error fields enter a message 4. To finish click on Apply 5.

Return to the list of rules, We can see that the rule has been added 1, it is in the last position, the rules being treated as on a firewall, that is to say starting with the top, the rule blocking access to PowerShell has no effect at the moment.

You must mount the ruler in the first position, select the 1 ruler by clicking on it, then in the Actions area, click on Raise 2 so as to place it above the others.

Now that the rule is on top of the rules that handle transfer with Exchange servers, PowerShell access is blocked.

To test the rule, it is possible from a browser to try to access the URL that publishes PowerShell, if it works, you should get an error message:

Now you know how to secure PowerShell access to Exchange by blocking it with ARR.
If you use IIS ARR as a reverse proxy to publish your Exchange servers on the Internet, I advise you to install Crowdsec on it to increase the level of security.