Introduction
In this tutorial, we will see how to configure the SSO on the Admin Center when it is installed as a gateway.
Installation as a gateway consists of installing the Admin Center on a Windows 2016 or 2019 server which is dedicated to administration.
Without the configuration of a constrained Kerberos delegation, the message is not possible to connect using the Use my account for this connection option and an alert message is displayed.
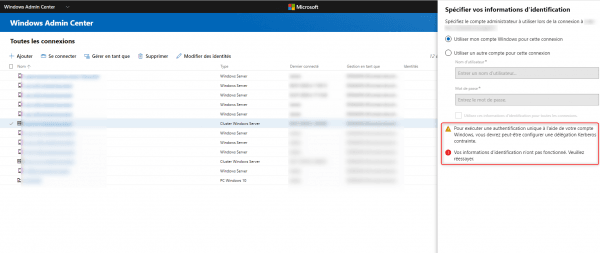
Configuring a constrained Kerberos delegation for SSO
The configuration is done in PowerShell from a domain controller.
To authorize a server:
Set-ADComputer -Identity (Get-ADComputer SRV-ALLOW-SSO) -PrincipalsAllowedToDelegateToAccount (Get-ADComputer SRV-ADMINCENTER)
To authorize several servers, use the script below to modify the $ServerWAC variable by specifying the Admin Center server and enter the servers where SSO must be configured in the $Servers variable which is an array.
$ServerWAC = "SRV-ADMINCENTER"
$Servers = "SRV-ALLOW-SSO-01","SRV-ALLOW-SSO-01"
foreach($Server in $Servers){
Set-ADComputer -Identity (Get-ADComputer $Server) -PrincipalsAllowedToDelegateToAccount (Get-ADComputer $ServerWAC)
}Validate the configuration
Also from the command prompt PowerShell, enter the following command by adapting the command to the server being tested:
Get-ADComputer SRV-ALLOW-SSO -Properties * | Format-List -Property *delegat*,msDS-AllowedToActOnBehalfOfOtherIdentity
The PrincipalsAllowedToDelegateToAccount property should display the CN of the Admin Center server and TrustedForDelegation should be true.
