In this tutorial, I will tell you how to harden password security with Lithnet Password Protection for Active Directory.
Lithnet Password Protection for Active Directory is a free utility that installs on domain controllers, which will allow us to increase password security with:
- Create a forbidden password dictionary, also taking into account the replacement of characters, for example if we forbid password, the password P@ ssw0rd! will also be banned.
- Prevent use of compromised password based on site basis haveibeenpwned.com.
- Prevent the use of the first and last name in the password by also using character replacement.
- Advanced password complexity management
- Using Regex for Passwords
Now that you know the mouth watering, we will see its installation, its configuration and its use.
- Installing Lithnet Password Protection for Active Directory
- "Basic" configuration of Lithnet Password Protection for Active Directory
- Configuring Group Policy to Use Lithnet Password Protection for Active Directory
- Test Lithnet Password Protection for Active Directory
- Lithnet Password Protection for Active Directory events
- "Advanced" configuration of Lithnet Password Protection for Active Directory
- Configure password complexity based on its length
Installing Lithnet Password Protection for Active Directory
Start by downloading the latest version available : Releases · lithnet/ad-password-protection and drop it on a domain controller.
Start the executable with a double click.
When launching the installation wizard, click on Next 1.
Accept the license 1 and click on Next 2.
Leave the default components, click on Next 1.
If necessary, change the location of the files, click on Next 1.
Confirm the installation by clicking on the Install 1 button.
Wait during the installation …
Close the wizard by clicking on Finish 1.
The installation is complete.
Even if this is not asking, I had to restart the server to take it into account.
“Basic” configuration of Lithnet Password Protection for Active Directory
For the configuration of Lithnet Password Protection for Active Directory, I will do it in two steps, I will first do a “simple” configuration in order to present the tool to you and then we will see how to have a more complete configuration.
The configuration is done in PowerShell, so you have to import the module using the following Cmdlet:
Import-Module LithnetPasswordProtectionTo illustrate the tutorial, we will add the password: password to the banned word. To do this, enter the command below:
Add-BannedWord -Value "password"
Before going any further, we will use the Cmdlet Test‐IsBannedWord to test if the password P @ ssw0rd is banned.
Enter the command:
Test-IsBannedWord -value P@ssw0rd
We can see that the command returns True, indicating that the password is banned
In the folder : C:\Program Files\Lithnet\Active Directory Password Protection\Store\v3\w onfinds the “databases” containing the passwords.
Configuring Group Policy to Use Lithnet Password Protection for Active Directory
To work, you must configure a group policy so that the settings of Lithnet Password Protection for Active Directory are applied.
Open the Group Policy Management console.

Right-click on the Group Policy Objects 1 container and click New 2.

Name the strategy 1 then click OK 2.
Right click on Group Policy 1 and click Edit 2.

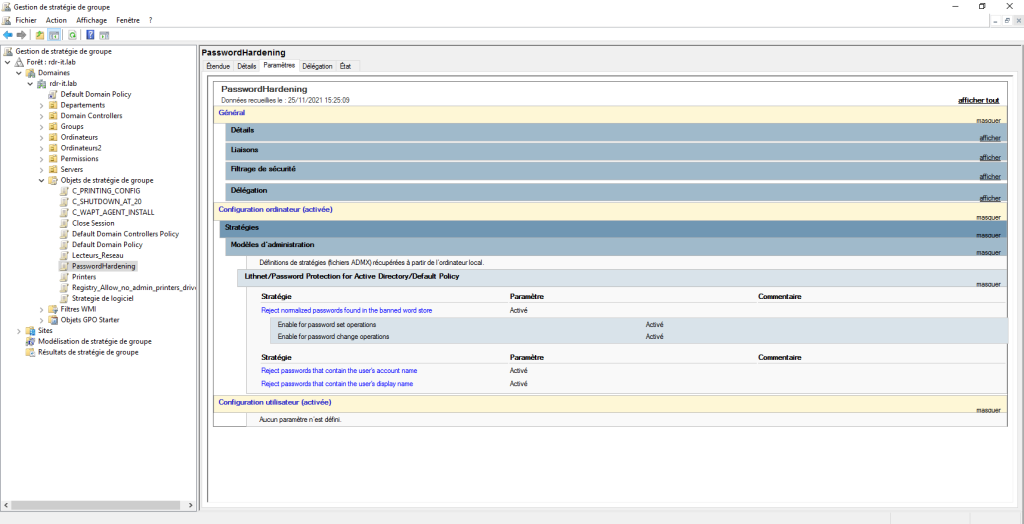
Go to the following location to access the settings: Computer Configuration / Policies / Administrative Templates / Lithnet / Password protection for Active Directory / Default Policy.

For the moment, we will only activate 3 parameters which will prohibit the use of the username, the user’s first and last name and banned passwords.
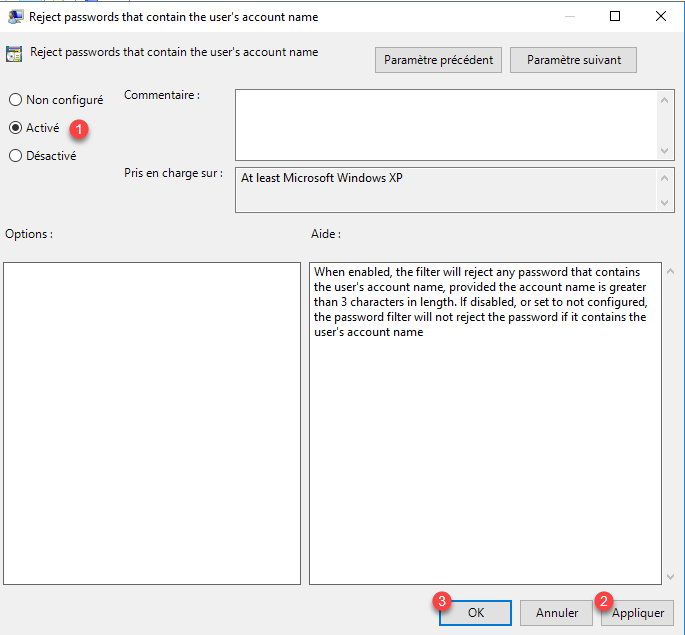
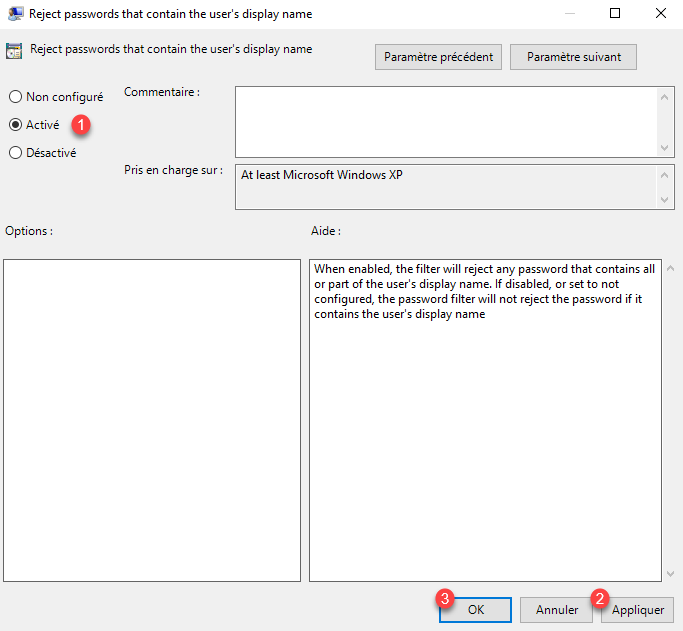
Open the Reject password that contain the user’s account name and Reject password that contain the user’s display name settings. For each one, activate the parameters 1 then click on Apply 2 and OK 3.
Open the parameter Reject normalized passwords found in the banned word store 1.

Activate the parameter 1 then check the boxes Enable for password set operation 2 and Enable for password change operations 3 if this is not done. Then click on Apply 4 and OK 5.

The two check boxes enable the option when creating the account and when changing the password.
Group Policy is configured.
Link Group Policy to OU Domain Controllers 1, right click on it and click on Link Existing GPO 2.

Select Group Policy 1 and click OK 2.

The strategy is linked to the OU.

On the domain controller, force the update of the group policies with the command gpupdate / force.
Test Lithnet Password Protection for Active Directory
To test Lithnet Password Protection for Active Directory, we will do it as follows:
- From the domain controller
- From a client computer
Here is the Password Policy (PSO) applied to user Batman.

From the domain controller with the Active Directory Users and Computers console
Right click on user 1 and click on Reset password 2.

Enter a password found in the list of banned passwords, for password, you can try password and P @ ssw0rd.
An error message is displayed indicating that the password is not valid.

Test from a computer
Now, we are going to test from a client computer, as if the user himself changes his password or that this one must change the password at the opening of the session.
How can we see it on the capture, I enter the password P@ ssw0rd.

As can be seen, the password is not valid.

Lithnet Password Protection for Active Directory events
On the domain controller, open the event viewer, then go to the Application log which is located in Windows Logs.
As can be seen in the screenshot below, there are different entries of the LithnetPasswordProtection application.

Still on this same capture, the selected line corresponds to the attempt to change the password on the Windows 10 client. We can read in the description that it was refused because the password is present in the database data of banned passwords.
For more information on the different events: Event logging and reporting · lithnet/ad-password-protection Wiki
“Advanced” configuration of Lithnet Password Protection for Active Directory
Now, we will see the “advanced” configuration.
Use the Have I Been Pwned password base
Importer la base Have I Been Pwned
Importing the database requires 40 GB available on the server.
The goal is to import the ntlm hash of compromised passwords, at the time of writing this tutorial, the file is 20 GB unzipped.
On this page : Have I Been Pwned: Pwned Passwords download the list of passwords in NTML format sort by hash.
Once download, unzip the archive, then open a PowerShell window and enter the commands to import the files:
Import-Module LithnetPasswordProtection
Import-CompromisedPasswordHashes -Filename "C:\tmp\pwned-passwords-ntlm-ordered-by-hash-v7\pwned-passwords-ntlm-ordered-by-hash-v7"

Adapt the path to your configuration
Wait during the import which can take 20 and 45 minutes depending on the server.
Test if a password is compromised
It is possible to test whether a password is compromised using the Cmdlet: Test-IsCompromisedPassword.
Test-IsCompromisedPassword -value iloveyou
We can see that the iloveyou password is compromised, the command return True.
Test if a user’s password is compromised
It is also possible to test if the hash of a user password is compromised with the Cmdlet : Test‐IsADUserPasswordCompromised.
Test-IsADUserPasswordCompromised -upn [email protected]
Here we can see that the hash of the password [email protected] is known.
Small precision, it is not because the hash of the password is in the Have I Been Pwned database, that the username / password pair is compromised, on the other hand if we recover the hash of the password during an NTML identification, we can deduce his password.
There is a script that allows you to test all Active Directory users here: Audit existing passwords · lithnet/ad-password-protection Wiki (github.com)
Prevent the use of compromised password
It is possible to prevent the use of compromised password by enabling the parameter: Reject normalized passwords found in the compromised password store.

The setting works the same as for banned passwords.
Configure password complexity based on its length
Lithnet Password Protection for Active Directory also allows to configure the complexity of the password according to its length.
For example: if the password is less than 8 characters, it must include letter + number + symbol, if the password is less than 15 characters, i.e. between 8 and 15, it can be dialed of letter + number (no symbol) and if the password is more than 15 characters no particular complexity.
The Group Policy setting to configure is Enable length-based complexity rules.

Lithnet Password Protection for Active Directory is an interesting solution to harden the password policy which allows to create a forbidden password dictionary.
Through this article I also want to thank the author Ryan Newington for the free availability of this tool.
I also invite you to watch his Github where he shares other program.